Supported by Thales Digital Factory, the group’s incubation programme, the start-up Chimere was inspired by the Tor network. Based on micro-segmentation and point-to-point connection of services and users, the Chimere team has redefined the principle of perimeter security. Its platform appears to be a relevant solution for all large enterprises.
The ingenuity of cyberattackers and the limits of « classic » perimeter defence are weakening the security of corporate networks. To strengthen their resilience, they must rely on an approach that isolates all internal network resources from each other, prevents any inbound flow and significantly reduces the risk of lateral movement by attackers. This is the objective of the start-up Chimere, whose platform allows users to benefit from a truly Zero-Trust Network Access (ZTNA). An original and relevant approach that aims to democratise the notions of zero trust and distributed trust.
How to implement a complete Zero-Trust?
In reality, there is a technology, not very recent and with a bad reputation, that integrates a mechanism that encompasses all the previously described characteristics. This technology is darknet technology. By studying its most well-known implementation (Tor), we realized that it had all the characteristics we were looking for, through its mechanism of hidden services.
Through an infrastructure exposed on the internet, it allows anyone to publish services and make them accessible only to users who have the cryptographic key necessary for any connection establishment: the « .onion » address. This address is not known to the network, only to users. It is essential for negotiating a connection with the associated hidden service.
The network also offers end-to-end encryption (in addition to onion encryption). Finally, it is a participatory network: everyone can add nodes to increase its size and robustness, without compromising its Zero-Trust characteristics. This is why attackers can take part in the network, without risk to the hidden services or users who access it. Exposing the network on the Internet then becomes acceptable.
Of course, Tor was not designed for this use. The Tor Project emphasizes the « respect for privacy » aspect. That’s why it was initially designed: to ensure the anonymity of users and services. In addition, the performance of the Tor network is known to be particularly weak. It was therefore unimaginable to use the technology as is for business needs: would organizations be willing to allow anonymous users to access their services through a connection reminding them of the 90s? They have monitoring and performance needs.
Therefore, we set about modifying the implementation to ensure a level of performance that could compete with the remote access solutions on the market, while adding monitoring that was initially nonexistent and created the Chimere network: an « ethical » darknet, capable of interconnecting users and services. Network administrators install Chimere agents within their IT, and on their users’ workstations. Through an administration console, itself hidden on the darknet and dedicated to each organization, they assign access rights to their services to their users with a few clicks, or revoke them in real-time. This principle of micro-segmentation and point-to-point connection of services and users redefines the perimeter security principle. It is now possible to isolate all resources of the internal network from each other, prevent any incoming flow, and significantly reduce the risks of lateral movements by attackers.
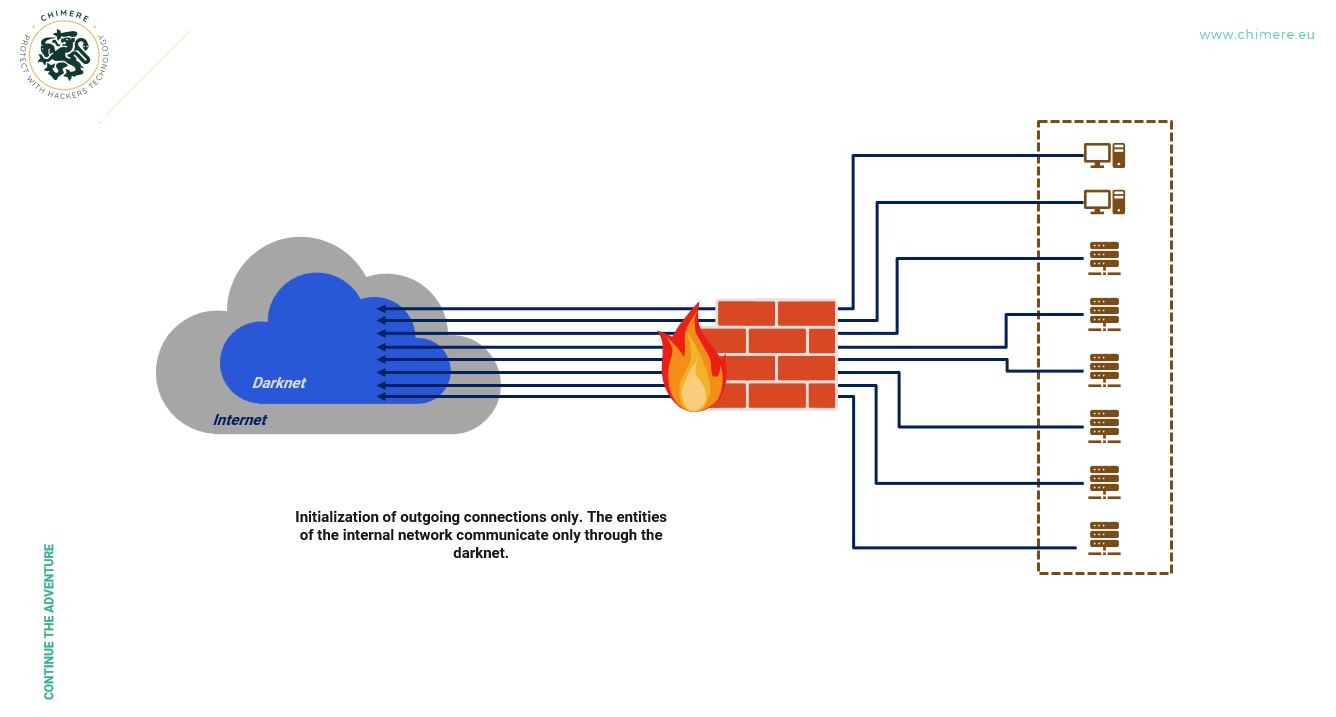
All these features are provided without having to trust the intermediary network, where other ZTNA market players require this trust from their customers. Thus, Chimere tends to use darknet technology, and more specifically the mechanism of hidden services to offer truly Zero-Trust ZTNA. Chimere’s darknet is a shared infrastructure among all its users, a separate darknet, completely uncorrelated with the public darknet, with its own rules and its own way of functioning. It is hosted on different public and standard clouds. Some providers are French, others not. Part of the elegance of the solution lies in the fact that its Zero-Trust aspect allows one not to trust the underlying infrastructure that hosts it, just as it is possible not to trust the operators of the nodes.
The circuits (paths taken by packets) are constructed by users and services before each TCP initialization. Thus, the path to take remains under the control of the connection initiator, allowing users and services to decide which part of the network they want to use. This type of functionality not only addresses performance issues by choosing only the fastest nodes at a given time, but also sovereignty issues. (Even if the network is Zero-Trust, some prefer to go through nodes exclusively French). With Chimere and the darknet principle, we want to reinvent the notion of secure interconnection and create a real community of businesses and organizations that will participate in the network to strengthen it. With this vision, we want to democratize the notions of zero trust and distributed trust.
Is this platform not aimed at the general public a priori? Who are your target customers and who are the customers already onboarded?
All companies with remote access needs or network segmentation needs will find relevance in using Chimere. However, we are aware that we are offering something that deviates from traditional cybersecurity solutions. As a result, we know that smaller companies that are just starting to be interested in cybersecurity and starting from scratch in this field will tend to opt for traditional solutions rather than innovative solutions, although we do have a few in our sales pipeline. We are always happy to welcome new ones and move forward with them! They bring us an agility and speed of execution that we rarely find among large accounts.
However, the main target at this stage remains large companies with a good level of maturity in networks and cybersecurity. These aspects allow them to be open to innovation and emerging methods such as ZTNA. Currently, we are mostly engaged with large players in defense, banking, or public organizations.
The darknet and anonymizing network technologies are often perceived negatively or associated with illegal activities. Is there a risk that this technology will be misused or diverted from its original purpose? How do you manage this in your offering?
Indeed, the darknet technology has a bad reputation. However, with Chimere, we are primarily interested in the mechanisms for publishing and accessing hidden services, which are to be distinguished from purely anonymity mechanisms. In other words, we use cryptographic mechanisms to ensure that services can only be accessed by users who have the appropriate cryptographic material (the famous onion address). On the other hand, we break anonymity.
On the one hand, we prevent the darknet from being used to hide the identity of users and therefore for malicious purposes, and on the other hand, this allows us to significantly increase performance. In fact, the anonymity provided by the darknet is initially achieved by passing messages through a series of nodes that make it up and through the use of as many encryption and decryption operations. These operations are costly and induce latency that is not acceptable to us. Thus, the modifications made to the implementation allow us to offer monitoring functions in our offerings. For example, it becomes possible for an organization to know which user is accessing which service, and to know its real IP address, something that is not possible in the initial implementation.
What are the short-term and medium-term developments for the Chimere project ?
Currently, Chimere can be installed on Windows user computers to access services, and on Linux servers for service declaration. The next projects will focus on the portability of agents to allow interconnections between Linux, MacOS, Android, and iOS users with Windows services. We are also working on interconnectivity with company directories to simplify the management of user access rights to services, and on the performance aspects of the darknet. At present, the network is not yet participatory, we are actively working on the aspects that will allow it to become a platform that everyone can claim tomorrow.